Original text
Contribute a better translation
The degree of confidence in the correct functioning of a system essentially determines the level of acceptance by users (and society in general) of computing systems in infrastructures that control physical (eg, factories, cars) or computer (eg, banking institutions) systems. ), whose malfunction may lead to damage-causing events (ie, loss of value).
Security can be addressed at all levels of the implementation of a computing system, from hardware components (eg, microprocessors) to software components (eg, operating system, applications).
There are companies (ie, Infineon) that offer a wide range of security implementation solutions at the hardware level (eg, TPM circuits, cryptoprocessors) that can be integrated into ICT systems.
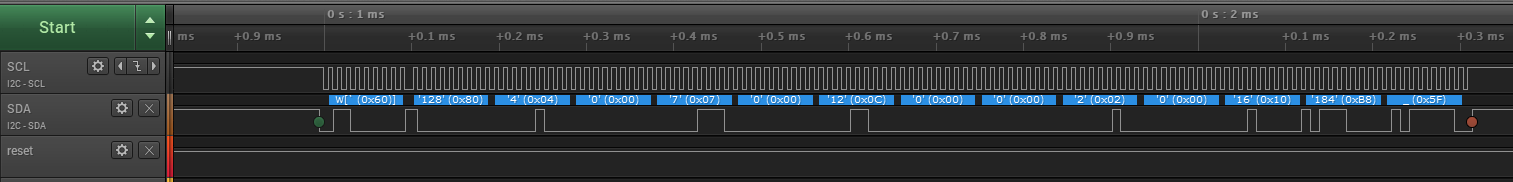
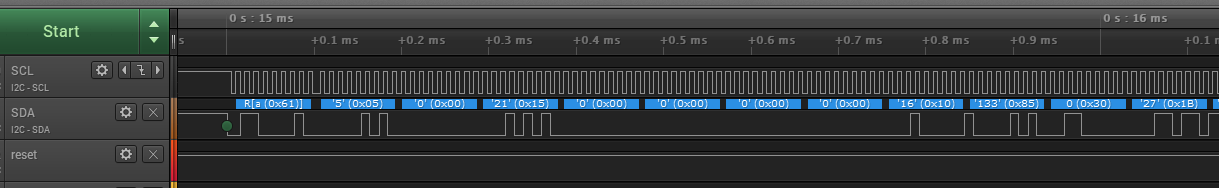
The laboratory experiment aims to introduce the basic elements for the interface between a microcontroller and a circuit that provides security services Infineon Optiga Trust E that is connected to the myocrocontroller via the I2C bus
- DAVE 4.3.2; - Infineon Optiga Trust E ; - (optional) Saleae logic analyzer 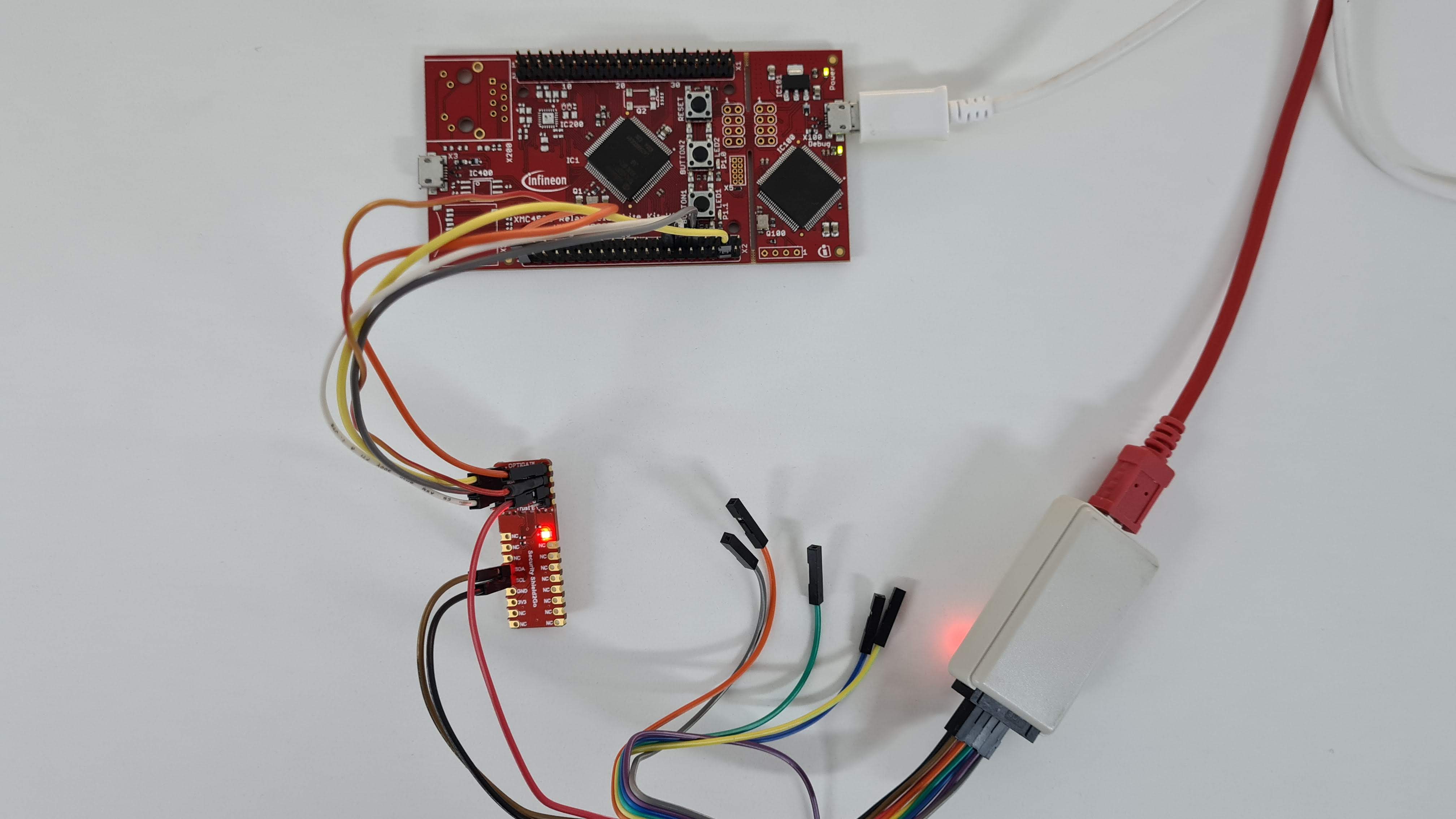
Or use the main.c file and the settings below 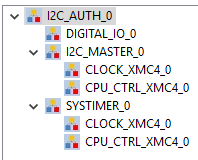 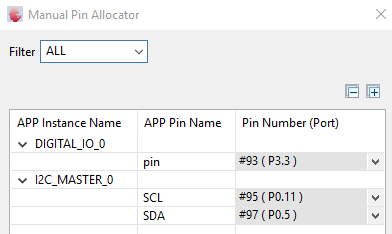 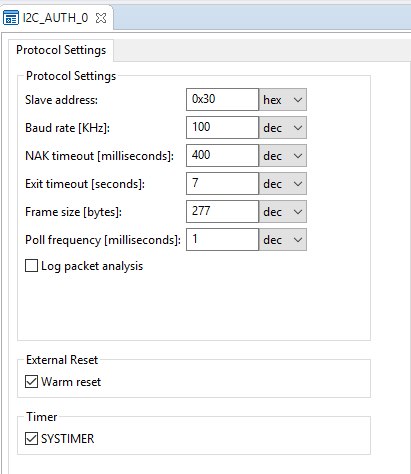 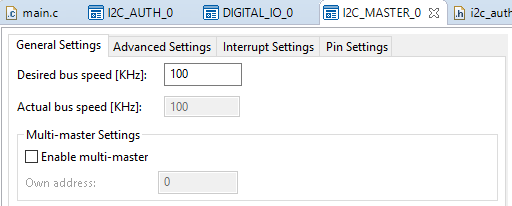 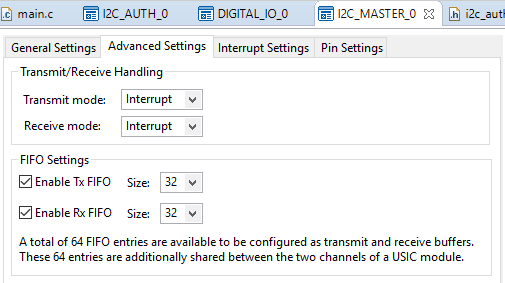 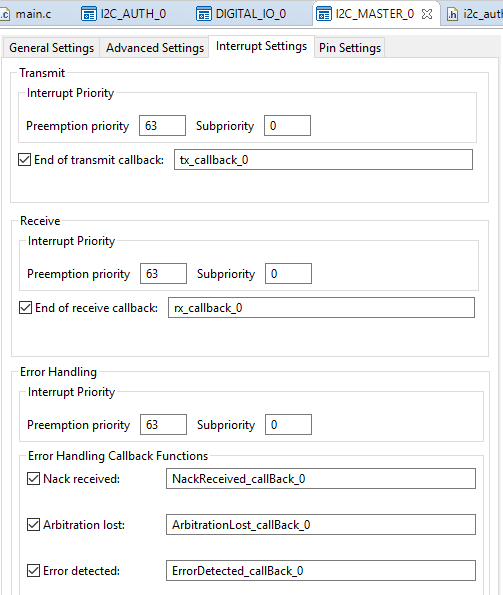 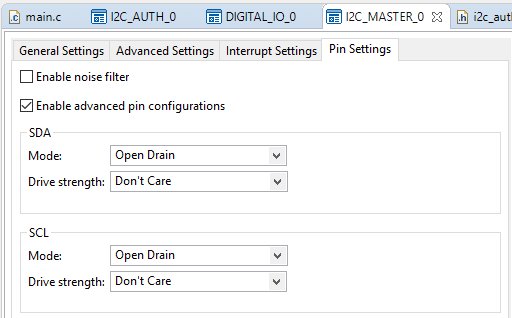
1. Make a program that will calculate the signature value of a message (string of bytes) using the SHA-256 algorithm implemented in the Optiga Trust E circuit. The message can be generated randomly. 2. Create a program that will calculate the signature value of a message (string of bytes) using the Elliptic Curve Key on NIST P256 curve algorithm implemented in the Optiga Trust E circuit. The message can be generated randomly. 3. Create a program that will allow you to generate a key pair (public and private) using the Optiga Trust E circuit 4. Make a program that will allow you to encrypt and decrypt messages using the Optiga Trust E circuit 5. Bring a function library to Dave security implemented at a high level (e.g.OPTIGA ™ Trust X Software Framework ), but which basically uses the services of the Optiga Trust E circuit.
|